3 Steps to Protect Private Information in the Workplace

The digital age is bringing people together in new ways.
More people than ever are working from home, over 92% of surveyed workers use the cloud for storing office data, and online dating has become so prevalent that a new word has entered the American lexicon: “zumping,” a portmanteau of “Zoom” and “dumping” to describe breakups over video calls.
As everything from social life to work life is quickly changing, managing your private information doesn’t just mean locking your birth certificate in a fire-proof safe anymore: it also means managing your online presence, storing digital documents securely, and communicating privately.
These steps are a guide to protecting private information in the workplace: identifying sensitive information, recognizing threats, and implementing winning strategies to keep your information secure.
Key Takeaways:
- Private information includes PII and non-PII information like names, credit card numbers, and browsing history.
- Security threats include social engineering and software exploitation.
- FileCenter protects and encrypts your digital documents to keep your private information secure.
Step 1: Identify Private Information
Private information in the workplace includes several different categories of information. Private information includes sensitive data relating not only to you but to your coworkers, colleagues, and clients.
The scope of private information in your workplace varies from industry to industry. In the medical field, HIPAA regulations include strict guidelines for how organizations can share and store medical records. In the finance industry, the Gramm-Leach-Bliley Act (among others) regulates how financial organizations use consumer data.
In every workplace, private employee information like Social Security Numbers, addresses, and phone numbers are necessary for various departments, from accounting to human resources to function.
In short, every workplace involves private information to a certain extent, and the first step to protecting private information is to identify the private information of your employees, coworkers, vendors, customers, and yourself.
Private information includes both Personally Identifiable Information (PII) and non-PII.
Personally Identifiable Information includes the types of information you may traditionally associate with private documents, such as:
- Name
- Birthdate
- Address
- Phone number
- Social Security Number
- Passport/Driver’s License numbers
- Credit card numbers
But in the digital age, PII also includes types of digital information such as:
- IP Address
- Device Serial Number
- Device ID
- Cookies
- Transaction Data
- Social Media Activity
Additionally, private information includes non-PII, such as demographic data, generalized browsing patterns, and aggregated trends.
To protect private information in the workplace, start by identifying what kinds of private information your workplace uses. Whether it be bank account information for thousands of clients or simply the employee ID you bring to work every day, protecting this private information is too important not to take seriously.
Step 2: Identify Privacy Risks
Once you’ve identified the private information your workplace uses, the next step is identifying the factors that risk your private information.
Social Engineering
Social engineering exploits human psychology to gain access to private information. Think of it as somebody trying to steal something valuable out of a house: they may either try to break down the door or pry open a window, or they might simply befriend the homeowner to get invited in. That’s social engineering: exploiting human behavior to gain access.
Social engineering is an increased risk today as online communication is especially susceptible to data breaches. In physical workplaces, examples of social engineering could include a coworker using a friendship with an administrator to gain access to private information they don’t have a legitimate business need to access, colleagues, sharing login credentials, and non-employees asking questions that involve the private information of others.
In the digital workplace, social engineering is an elevated risk. The most prominent risk is phishing, the activity of posing as a legitimate actor to gain access to private information. A common form of phishing is to request passwords and other sensitive information by email while impersonating a trusted organization like Microsoft or Google.
Versions of phishing include terms like spearfishing (phishing that targets specific individuals) and whaling (phishing that targets executives with high-security access, such as CEOs and CTOs).
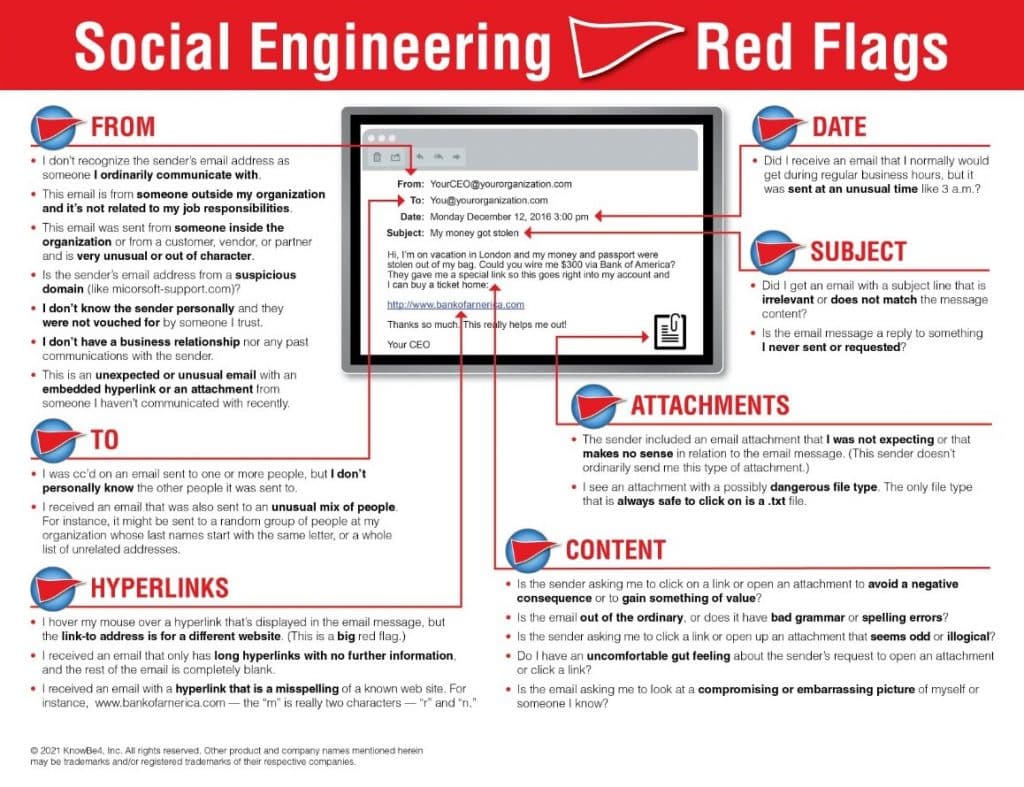
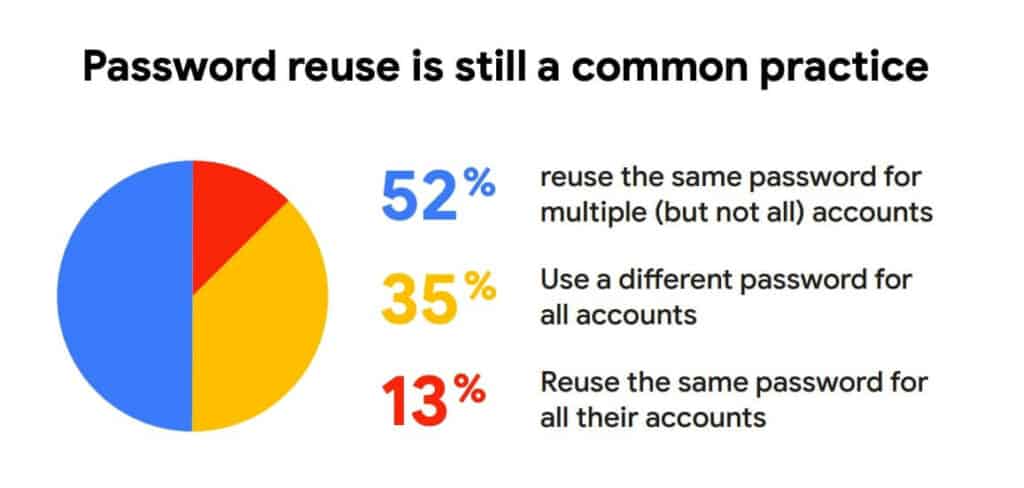
Weak or Reused Passwords
Twenty-three million people use the password “123456.” Nearly a quarter of Americans use passwords such as “password,” “12345,” and “qwerty.”
Activities that increase password vulnerability risks include using the same password for multiple online accounts, using weak passwords, sharing passwords with others, and recording passwords on paper. Password vulnerabilities are a major risk for protecting personal information, whether it’s due to social engineering, hacking, malware, or data breaches from sites you use the same passwords for.
Software Vulnerabilities.
Your digital presence is a cornerstone of your business, but these new tools also create new vulnerabilities.
If hacking and malware are like breaking into a house and social engineering is like befriending the owner, a software vulnerability is like forgetting to close the front door. Software vulnerabilities can range from misconfigured settings to exploits like privilege escalation.
Although software development and administration may seem mundane, failing to take it seriously can result in serious consequences. In 2021, Facebook leaked the phone numbers and other personal data of 533 million users simply due to misconfigured software settings.
Step 3: Security Controls
Although it’s impossible to completely eliminate the risk of private information breaches, there are tangible steps you can take to protect your security.
Physical Controls
While many of these information risks are digital, mitigating these risks begins with physical security. What does this look like for your workplace?
Using employee IDs is essential to distinguish between legitimate users and malicious actors. Security controls like key fobs, access codes, and physical locks and keys are all tools that can help keep your workplace physically secure.
You should store physical documents containing sensitive information in secure locations such as a locked filing cabinet or briefcase. You should always keep non-essential private information out of the workplace. Keep it at home in a firebox or safe whenever possible.
Computers should always be password protected, and users should log out every time they walk away from their screen—even if it’s just for a few minutes!
Digital Controls
You wouldn’t let a stranger walk in from the street and browse through your filing cabinets, so you shouldn’t accept that treatment of your digital documents either. Document management software is an essential tool for keeping your private information secure.
Document management software allows you to access your digital files remotely, but the essential characteristic of document management software is that it allows only you to access your files. This technology allows you to restrict access so that only you and your team can view sensitive information, but unauthorized external users have no way of accessing that information.
Encryption is also an essential digital control. Encryption disguises plain text as scrambled code that a user can only decode with a specific decryption key. That means that even if your data were to fall into the wrong hands, they wouldn’t be able to access the readable text unless they also procured the specific key.
FileCenter’s Document Management Software
Managing all of the ins and outs of privacy and security is a handful, but thankfully there are powerful tools that businesses and individuals can use to keep their private information secure.
One of these tools is FileCenter.
FileCenter is a document management platform that gives users access to a wide range of documentation tools such as PDF editing, optical character recognition, automated routing, and file format conversion.
To learn more about how FileCenter can help keep you safe, schedule a demo or download a free trial today.


