The No-Nonsense Guide to Storing Documents Online Securely

Documentation has changed.
Humanity has progressed from drawing cuneiform in clay tablets to storing emojis in the cloud, and in the process, online document security has emerged as a perennial priority for modern businesses.
For as long as innovators have been discovering better ways to record and store documents, successful businesses have been taking advantage of the strengths and weaknesses of each new medium.
Today, online documentation is on the leading edge of document management technology, allowing businesses to adapt and thrive. Online documents are efficient and effective, but they also come with their own security risks. This guide will cover the largest threats to your online document security, as well as some essential steps you can take to store documents online securely.
Key Takeaways:
- Online documents come with unique security risks like phishing and malware.
- Using strong passwords and tiered access helps keep your documents away from unauthorized users.
- Encryption hides the contents of your documents so that only users with the decryption key can read them.
Overview of Online Document Security
Despite already having a storied history, cybersecurity continues to advance in leaps and bounds. With the prevalence of the internet, storing documents online securely presents some unique challenges that modern businesses should take into account.
Phishing
This is the practice of using social engineering to access private information. Today, phishing often involves fake emails or phone calls where a fraudulent third party may impersonate a reputable company or even a specific person.
Back in the mid-20th century, tech enthusiasts reverse-engineered a way to replicate the tones that phones at the time used to route long-distance calls, essentially allowing them to call anywhere in the world for free. They called themselves “phreaks,” a portmanteau of “phone freaks,” and while modern telephone protocols have made phreaking obsolete, its signature “ph” still lives on in “phishing.”
Today, rather than impersonating legitimate dial tones, phishers impersonate legitimate business communications to gain access to private information ranging from credit card numbers to company secrets. Modern phishing includes several varieties, such as “spear phishing,” in which a cybercriminal targets a specific individual, or “whaling,” where the target is a high-level executive within a company (such as an owner or CEO).
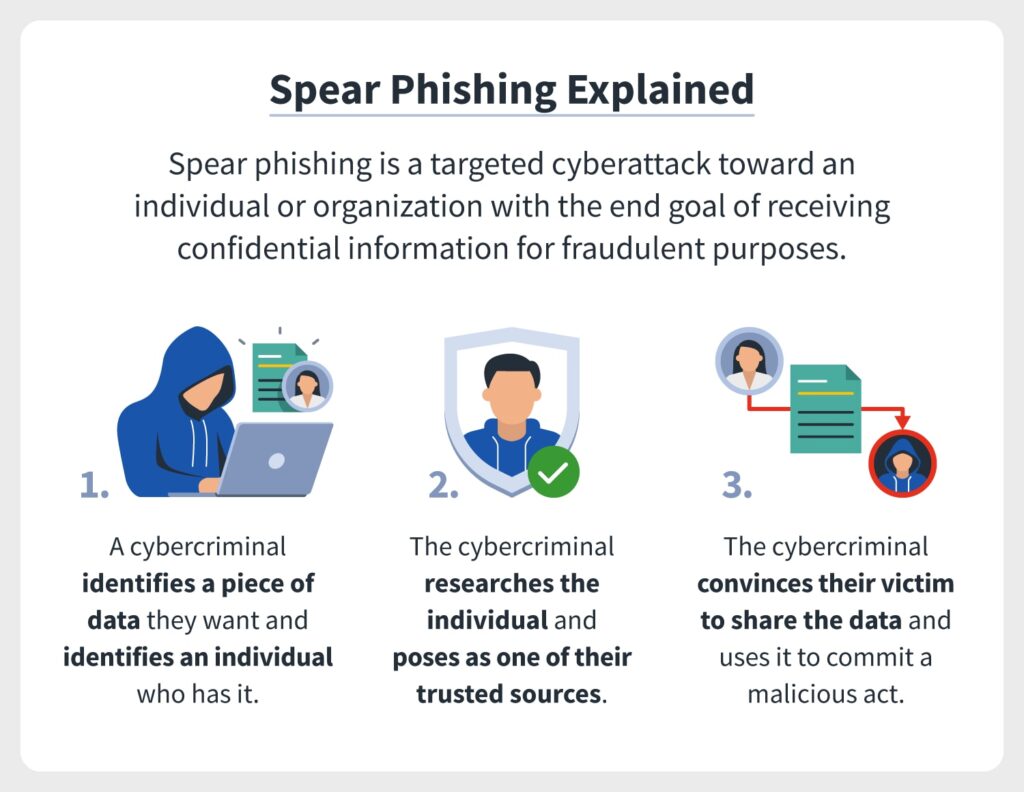
Malware
A portmanteau of “malicious software,” malware is any software designed with malicious intent. “Malware” is a broad term that encompasses everything from jokeware (software that impedes the user for mostly harmless or comedic effect) to computer viruses, which can corrupt and shut down entire systems.
Some types of malware are obvious, while others are more subtle. For example, ransomware is unsubtle – this type of malware holds an infected system hostage until the user pays a ransom. While this kind of malware is still dangerous, users at least know what is happening. On the other end of the spectrum, some malware silently creates backdoors, which allow malicious actors to access the system undetected.
Hacking
Technically, “hacking” is any activity that seeks to gain unauthorized access to data, which means that phishing and malware are both examples of hacking. However, these aren’t the only kinds of vulnerabilities that you should protect your online documents from.
Hackers can also gain access to your online documents by brute-forcing passwords, taking advantage of security exploits (such as escalation of privilege), or disrupting your system (such as through denial-of-service attacks).
In other words, your online document security has to account for a large variety of threats that range from the relatively mundane to the catastrophic.
Password Protection
You use a key for your house, a code for your safe, but what about your online documents?
In a way, securing a car or a personal computer is simpler than securing your online documents. This is because the access rules are simple: only a limited number of people are allowed to enter, so as long as nobody else acquires a key, your property is secure.
Online documents are less like a safe and more like a safety deposit box where access is staggered: some people may be allowed to access the vault, but only certain boxes within it. Online documentation is similar in that regard – users should have access to all the documents they need but none of the documents they don’t.
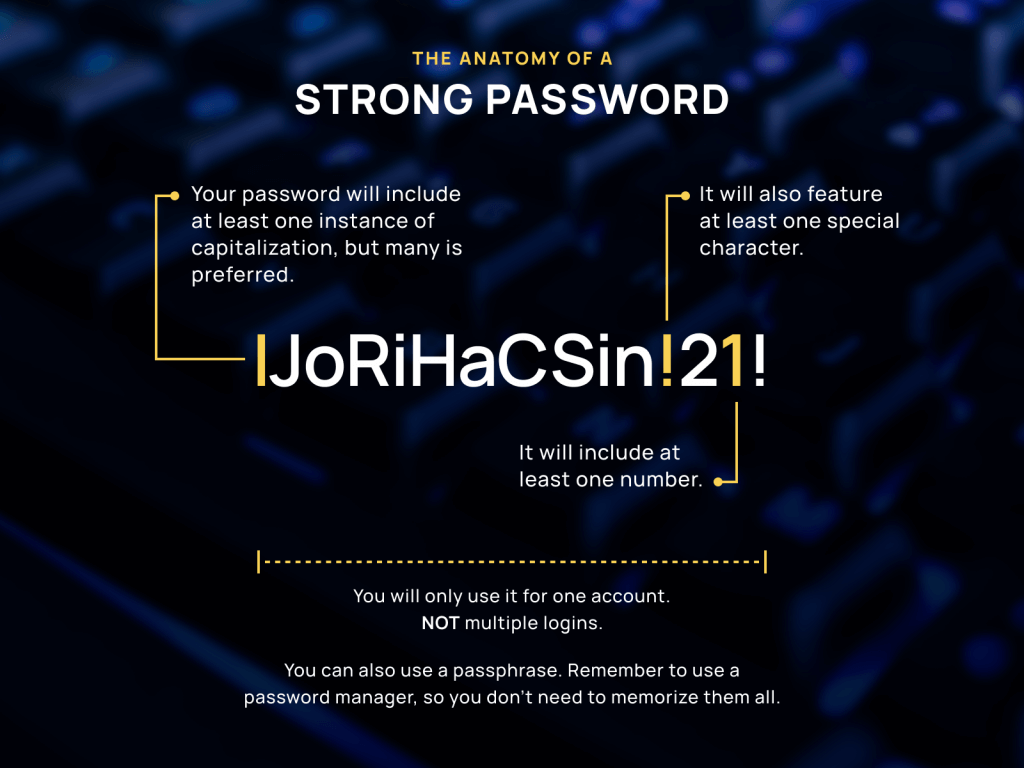
The first step to securing your users’ access to documents online is enforcing the use of secure passwords. Your passwords should be at least 12 characters (though longer is better), include a combination of upper-case and lower-case letters, numbers, and special characters, and should avoid any “easy-to-guess” clues such as your name.
To further protect your online documents, use tiered access by password-protecting sensitive PDFs. There are several ways to password-protect your private documents either natively in your PDF software or within your document management software.
Encryption
There are two ways to send a secret message:
- First, by sending a message that anyone could understand, but only the recipient can see.
- Second, by sending a message that anyone could see, but only the recipient can understand.
Encryption emulates the second approach by encoding messages with an encryption key so that any unauthorized user would only see a scrambled code, while authorized users who have the decryption key can convert the encoded message back into its original format.
Of course, the best approach to security is to incorporate both techniques. Use password protection to prevent unauthorized users from accessing your stored documents, but use encryption to make sure that shared documents are equally secure.
For example, if you draft a contract for one of your vendors, you don’t want just anybody to be able to read it. To stop unauthorized users (such as competitors) from accessing the contract, password-protect it. But to ensure that even if bad actors manage to access it, they won’t be able to read it, use encryption.
In online document security, encryption is especially important. As opposed to your local hard drive, you don’t have the option of simply disconnecting from the internet to keep unauthorized users at bay. Encryption is an extra layer of security so that your online documents are more difficult to intercept and interpret.
Store Documents Only Securely with FileCenter
Password protection and encryption are just a few of the tools FileCenter uses to help you get the most out of your documents.
With features like PDF editing, conversion between common file formats, optical character recognition, and encrypted sharing portals, FileCenter allows you to maximize your efficiency and security.
Are you interested in boosting your online document security but not sure where to start? Frustrated with your document management process and don’t know how to improve it? FileCenter can help.
Start your free trial today to see how FileCenter can revolutionize your document management.


